Any human being is distinct from another through various physical attributes. It includes the face, fingerprints, hand geometry, handwriting, iris, retinal, vein, and voice. A biometric device is a device that can distinguish and identify people based on any of the previously mentioned physical attributes. Biometric information is different from personal information like name, age, address etc. Biometric information cannot be used to find out personal information.
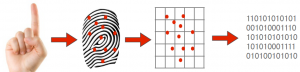
With the introduction of Aadhar card in India, most people are now familiar with what a biometric device is. Biometric devices are gaining popularity with more and more offices using a biometric fingerprint scanner to maintain attendance of employees.
One might wonder why we have fingerprints and how they are unique. Fingerprints are there to improve our grip on objects. The ridges on the finger create extra force of friction between the object and our hand so that we can hold onto the object. Fingerprints are formed in the womb when the child is about seven months old. The pattern of the fingerprint is randomly created based on our DNA. This makes each individual’s fingerprint different from another one. Identification of an individual based on his or her fingerprints is known as Dactyloscopy.
So how does a fingerprint scanner work?
Before computers were used to match fingerprints, they had to be manually matched. Sir Edward Henry of Metropolitan Police London used a system to match fingerprints where sixteen features of two fingerprints needed to be matched to be considered as from the same source. In the United States, only eight features need to be matched. With the introduction of computer and special biometric electronic devices, the system changed.
A fingerprint scanner basically has two different jobs. It needs to scan the fingerprint and then it needs to match it with the stored fingerprints. The fingerprints are not stored in a biometric device as an image as this may cause security issues. Instead a fingerprint is converted into a mathematical representation of the important and unique features of the fingerprint and stored in the system. When a fingerprint is scanned, it is converted into a mathematical representation which is then matched with the existing database of encrypted representations. The encrypted keys cannot be reverse engineered to create a fingerprint.
Fingerprint-based access and attendance systems have several benefits over the other forms of access and attendance systems like card-based or password based systems.
- A fingerprint cannot be duplicated.
- A fingerprint cannot be guessed like a password
- A fingerprint cannot be misplaced like an access card
- A fingerprint cannot be forgotten like a password
Besides access and attendance systems several other uses of fingerprint-based identification system have emerged. There are laptops and smartphones that are based on fingerprint-based locks and a few banks have introduced ATMs that have fingerprint identification system.
Interesting post, Thanks for sharing.